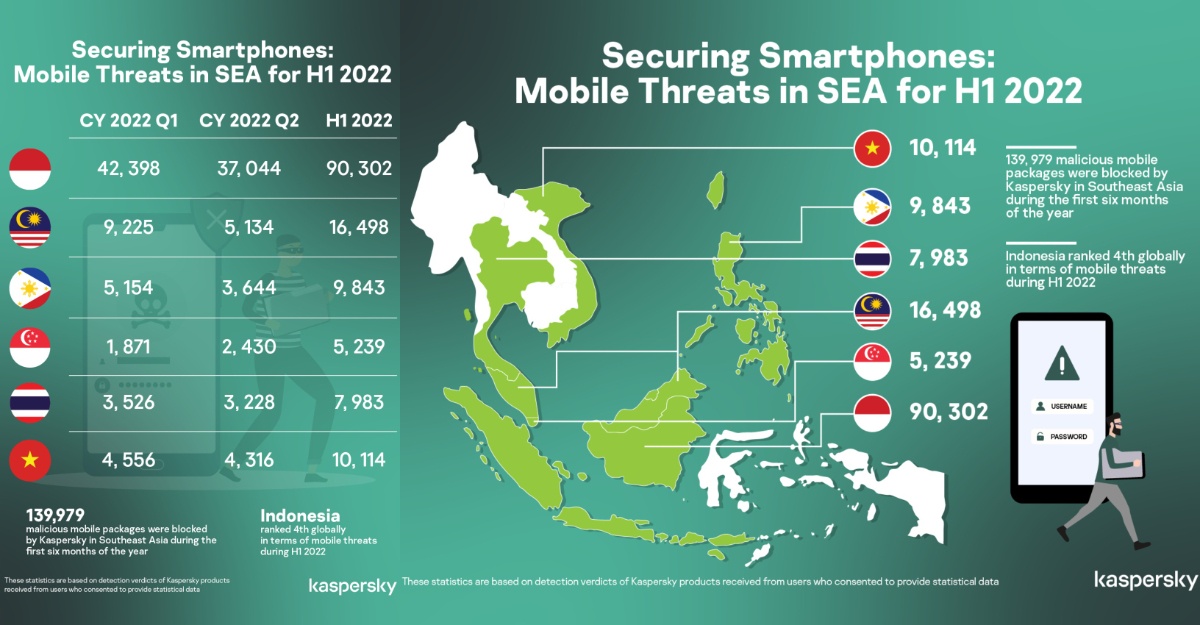
Kaspersky, the global cyber security company, released its latest data about mobile malware consistent decrease in number in Malaysia. During the period of January till June this year, the mobile malware was detected 14,359 times versus 45,267 in the same period 2021, dropping by 63.55% (excluding adware and risk ware).
Malaysia has seen a downward trend of mobile malware attacks gradually. In 2019, 145,044 attacks on Malaysian users, subsequently 103,575 in 2020 and 71,889 in 2021.

Mobile devices are another route for malware to enter the corporate network. Most businesses have invested in security that protects all endpoints within their corporate network – plus firewalls that prevent unauthorized external access to corporate systems. However, enabling access – to business systems and data, from mobile devices – means smartphones and tablets will effectively cross through the protective firewall. If those devices are infected with mobile malware, that will introduce security issues within the corporate network.
This set-up also poses dangers from mixing corporate data and personal data on one device. Whenever personal data and corporate data are stored in the same mobile device, there’s the possibility of security risks. Separating corporate data and the user’s personal data can help businesses to apply special security measures for their confidential or business critical information.
Moreover, high-profile employees can become a victim of cyber-espionage. For instance, in 2020 Kaspersky found a new Android implant used by Transparent Tribe for spying on mobile devices. It was distributed in India disguised as a porn-related app and a fake national COVID-19 tracking app. The app was able to download new applications to the phone, access SMS messages, the microphone, call logs, track the device’s location and enumerate and upload files to an external server from the phone.gather
Transparent Tribe is not the only one example; other similar campaigns were detected by Kaspersky researchers over the years – for example, such as GravityRAT, Origami Elephant and SideCopy.
Despite the global and regional decrease in mobile malware number, attacks are becoming more sophisticated in terms of both malware functionality and vectors. Kaspersky researchers have seen new and old players continue to be active on the cyber threat market. One of the most dangerous of all in this regard is banking malware.
“Our security experts recently revealed active cyber criminal campaigns targeting mobile device users here in our region – Harly, Anubis and Roaming Mantis. Harly is a Trojan subscriber targeting users in Southeast Asia countries. It signs up for paid services without the user’s knowledge. Anubis combines mobile banking Trojan with ransomware functionalities to squeeze more money out of their victims while Roaming Mantis, a notorious gang, is actively targeting both Android and iOS users,” said Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky.
Kaspersky prevented 149 attempts to exploit mobile banking users in Malaysia during the first half of 2022. Vietnam was on the top of chart amongst the Southeast Asia peers with 182 detections, with Malaysia ranked second.
BYOD also brings you even more platforms to manage. With the average employee now using two or three different mobile devices to access the corporate network, BYOD brings IT and security departments the challenge of having to implement and manage mobile security across an almost limitless range of devices and operating systems, including: Android, iOS, Windows Phone, Windows Mobile, BlackBerry, and Symbian.
The main idea behind proper BYOD security is that personal devices have to be treated in the same manner as company-owned devices. Likewise, laptops and smartphones being used outside of the company perimeter have to be protected just like those behind the firewalls and network protection solutions in the office. Some traditional methods are not applicable anymore, like, for example, web control enforced centrally for the corporate network only.
“This goes to show that regardless of the type of device we use, cyber criminals can infect our smartphones, steal all data and money in them, and even access or even wipe out our messages, emails, private photos and, more. With the hybrid remote work which also allows employees to access their work mails through their mobile devices, the risks extend from individual to a wider enterprise-level breach. Such can be avoided if we do the basic act of installing legitimate security solutions in our smartphones,” adds Yeo.
An IT department has to keep in mind that in the modern environment employees will work with corporate data anywhere they want, on a variety of devices. What has to be done is proper control of software and apps, web and e-mail as well as protection from malware and loss/theft using modern methods.
To help enterprises secure their data amidst a post-pandemic BYOD set-up, Kaspersky experts suggest:
- Automatically enforced security policy. Company rules are inefficient if they are just printed and signed by employees. A worker does not have to think if a certain app or website is appropriate, restricted or plain dangerous. He or she is usually not an expert in this. Automated control on software, devices and web is the only solution to prevent accidental loss of data.
- Inventory. The IT department has to know exactly which devices are allowed certain privileges to access corporate data, and be able to revoke the access rights or block the device completely.
- Beyond anti-malware. When talking about protection from threats, effective, industry-leading anti-malware protection is a must, but it alone cannot guarantee security. While a traditional anti-virus engine is fine with generic malware, targeted attacks require more sophisticated techniques. Among them are solutions designed to directly combat new and unknown exploits, vulnerability assessment tools and frameworks that will automatically install and control software and push updates for critically vulnerable applications.
- Mobile Device Management. A security policy has to be enforced on all devices, regardless of platform, and traditional business security suites are not capable of applying the rules and security features for smartphones and tablets. Modern mobile platforms like Android and iOS do have to be supported, and managed centrally just like traditional laptops.
- Further protection of data using encryption. It reduces the chance of sensitive data loss even in a case where a personal device was compromised or stolen.
Top 5 types of mobile malware detected in H1 2022 in Malaysia
- Trojan
- Trojan-Downloader
- Trojan-Spy
- Trojan-Dropper
- Trojan-SMS